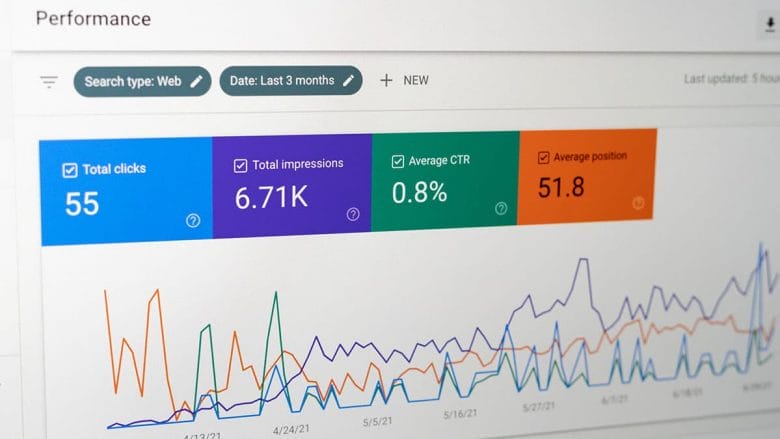
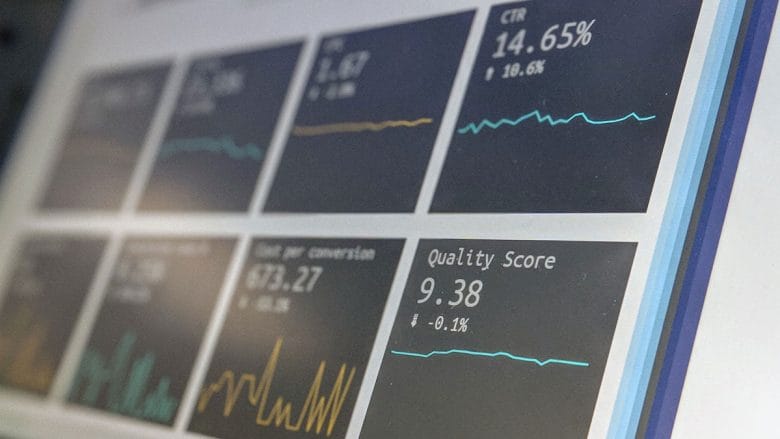
How to Optimize WooCommerce Product Images for SEO?
Nowadays, WooCommerce is the most famous and hugely used platform to establish an eCommerce business. It provides flexible, potential, and highly optimized online shopping solutions. To create a successful and famous online store, you must know how to optimize WooCommerce product images. Ensuring a better perspective about your product’s image quality and resolutions is very important. Product images create the first impression to the customers about products before buying something. WooCommerce product image optimization is essential to improve revenue and …