The business world has greatly evolved over the last decade. Nowadays, people work from home and still manage to deliver the expected results. Recently, many people around the world have also been trying to work from home due to the COVID-19 outbreak. Therefore, we’re all living in times when it’s vital to know how to work from home. For all their remote work one tool that most workers use today is a VPN. In this article, we’ll look at the most vital features to look for in a VPN to help ensure you get the effective one. So, read on.
What’s a VPN, and what do you need it for?
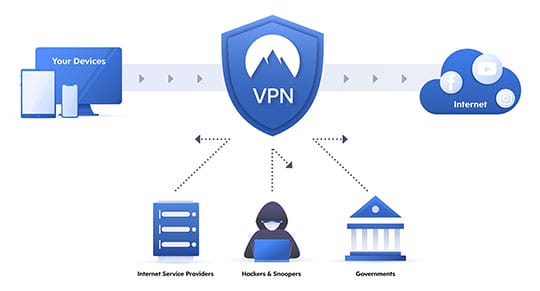
A VPN (Virtual Private Network) is special software that secures your data and protects you against hackers when browsing online. You can also use it to access some blocked sites, and hide your online activity from cybercriminals, especially if you connect to a public WIFI.
Now that you know what is a VPN, and its uses, let’s look at the most critical features that make a good one, shall we?
Recommended for you: VPN vs Proxy: What are the Differences? Which One is Better?
1. Technical Security
 Some of the best VPN services in the world are always willing to discuss the measures they’ve put in place to ensure users are safe. Any high-quality VPN will offer you the latest and most secure encryption, strong protocols, and extra security features like Tor compatibility and split-tunneling.
Some of the best VPN services in the world are always willing to discuss the measures they’ve put in place to ensure users are safe. Any high-quality VPN will offer you the latest and most secure encryption, strong protocols, and extra security features like Tor compatibility and split-tunneling.
VPN encryption is among the most significant features that you should look for. Basically, encryption refers to converting your data in a more complex format that other people can’t figure out. This explains why most professionals love a VPN with great encryption, as it keeps their crucial files safe.
Symmetric key encryption and public-key encryption
The two major encryption types that you should know about are symmetric key encryption and public-key encryption. Symmetric encryption mostly involves the sharing of one key by your device to encrypt and decrypt data. If other people don’t have that exact key, then they can’t access your data. This means better security.
Public key encryption is quite different since every device has to use a public-private key combination. So, one device uses your private key to help encrypt the data, while the second computer decrypts it with a public one.
HTTPS, TLS & SSL
If you spend most of your time on the internet, then you have noticed the “HTTPS” (wiki) on your address bar. This is considered a sign of a safe site since it shows that the website uses TLS (Transport Layer Security) and SSL (Secure Socket Layer). TLS mostly relies on SSL. So, SSL combines both public and symmetric key encryption to provide effective security.
TLS and SSL might not always be effective, which is where PFS comes in (wiki). For PFS, you use a unique encryption key for every session. The key is always deleted after the session. So, even if hackers had already found a way to enter the session, they still can’t access your files since you’ll be using different keys every time.

Other factors
In addition to technical security, it is important that you choose a VPN that allows anonymous payments. This is because there is a comprehensive policy concerning disclosing vulnerabilities.
Poor quality VPNs are more likely to leak your IP and DNS. If this happens, then your ISP or any other person with access to your network can notice these leaks and use them as an opportunity to attack your computer. Therefore, if you see that a VPN leaks your IP and DNS, then it’s useless as it can’t guarantee privacy.
Ultimately, any secure VPN service should have excellent and sophisticated measures to ensure your data is safe when you’re browsing the web. It’s vital to test any VPN for leaks before using it. You can also check whether respected third-parties recognize that VPN and validate its efficacy in providing online security.
2. Privacy Policy
 Evaluating the privacy level that a certain VPN offer is among the most vital things that you need to do. What makes this step so critical is the fact that many VPNs in the market today promise excellent privacy but do not deliver that eventually.
Evaluating the privacy level that a certain VPN offer is among the most vital things that you need to do. What makes this step so critical is the fact that many VPNs in the market today promise excellent privacy but do not deliver that eventually.
An effective VPN should have a zero logs policy. What this means is that the VPN promises not to store any information except your login details. So, no usage information, timestamps, or any identifying information will be stored by that VPN. By choosing a VPN service with a zero logs policy, you can guarantee that any critical information regarding your projects won’t fall into the wrong hands in any way.
There are different types of logs policies. They include:
A. Usage Logs
These logs usually store the information collected when you are using the internet, such as your IP, connection times, and history. Usage logs are mostly associated with poor-quality or free VPNs.
B. Connection Logs
Connection logs usually collect data regarding how you hide your IP address. Therefore, if you have used a VPN to hide your address and appear to be in different places around the world, then this information will be found in these logs.
C. Error Logs
Error logs mostly keep information regarding the errors you get when using your VPN. Although your username and IP address might also be collected, you don’t need to worry since these logs are used to help improve user experience.
A VPN might also store the server load, server location, or bandwidth usage. This information is usually used to ensure the effective provision of the promised privacy. So, it’s crucial that you ask the exact type of data that a certain VPN collects. That way, you can be sure whether it’s what you need, especially if you mostly deal with very classified projects that need heightened privacy.

If a VPN service is not willing to provide all the information about the data it records both before and after the session, then it’s probably not worth it. You can also look for some online VPN reviews to help you see whether that VPN service has a record of not providing the privacy level it promises. That way, you can be sure whether the VPN will work for you.
If you are offered the privacy policy by a VPN service, then go through it entirely and carefully. Doing that enables you to see what type of data the VPN keeps, hence allowing you to easily decide whether to choose it or not.
You may like: Should You Opt for Antivirus Software or a VPN? Let’s Find Out!
3. Location and Jurisdiction
 Location and jurisdiction are two factors that you can easily overlook. All VPN providers are always bound to certain regulations. Thus, it is important that you know all these rules and how they can affect your privacy.
Location and jurisdiction are two factors that you can easily overlook. All VPN providers are always bound to certain regulations. Thus, it is important that you know all these rules and how they can affect your privacy.
Typically, you shouldn’t worry about your jurisdiction if your VPN is effective. Instead, you must find out if your VPN provider has a clear procedure for responding to authorities in case they ask about its logging policy. You should also check if the VPN service has a warrant canary and other stated measures on the website. That way, you’ll be sure if the crucial information from your clients will be safe even if anyone accessed the site.
It is also wise to check where the VPN provider is based, that country’s laws, and if the company has any history of being in trouble with authorities. Doing this enables you to avoid risky companies and pick the best service.
More importantly, you should look for a VPN that allows you to connect to locations outside the 5,9 and 14 eyes. Locations inside these eyes are always under surveillance, making it hard to stay anonymous. Also, your client’s critical data might be more exposed if you use a VPN that does not allow locations outside 5 eyes and the rest.
4. Ownership and Business Model
 It is usually expensive to start and run a reliable VPN. Some free VPN providers choose to collect data like emails and sell it to help subsidize the costs. Other VPN services only rely on advertising, which is not great for a user’s privacy. As much as possible, you should stay away from free VPNs as they will put your security at great risk.
It is usually expensive to start and run a reliable VPN. Some free VPN providers choose to collect data like emails and sell it to help subsidize the costs. Other VPN services only rely on advertising, which is not great for a user’s privacy. As much as possible, you should stay away from free VPNs as they will put your security at great risk.
It is vital that you ask the VPN provider to clearly explain how they make money and how financial details get processed. A good and trustworthy VPN should only be making money through user subscriptions and not selling of vital data. So, remember to always check who owns the VPN, and if you can trust it with your most crucial details like account numbers when sending them to your clients and bosses.
One red flag you must look out for is a company whose legal and brand names do not match. Such shows that the provider can’t be trusted. You should also find out whether other entities invest or control the VPN’s services. Make sure you research if these companies have also invested in other products and whether they share any information between them. This will help you get more details and enable you to choose the most trustworthy provider.

5. Large Device Coverage
 You need to ensure the VPN you choose can run on any device you want from PCs to Android phones. It can be very disappointing to pay for a VPN service to help you work more comfortably and safely, only to find that it doesn’t work on your device. So, ensure you look for a VPN that you can use on your phone in case your laptop has issues. That way, you can progress with your work easily and avoid any inconveniences in the future.
You need to ensure the VPN you choose can run on any device you want from PCs to Android phones. It can be very disappointing to pay for a VPN service to help you work more comfortably and safely, only to find that it doesn’t work on your device. So, ensure you look for a VPN that you can use on your phone in case your laptop has issues. That way, you can progress with your work easily and avoid any inconveniences in the future.
6. Huge Server Network
 A huge server is among the best factors that make a VPN excellent. Having a large server network will help you unblock any restricted sites and allow you to get all the information you are researching for your client’s project. Also, an excellent server network can help you to connect to nearby servers and boost your internet speed.
A huge server is among the best factors that make a VPN excellent. Having a large server network will help you unblock any restricted sites and allow you to get all the information you are researching for your client’s project. Also, an excellent server network can help you to connect to nearby servers and boost your internet speed.
7. Speed
 Paying for a VPN service that has great speeds is vital when it comes to working remotely. A high-quality VPN should ensure your work data flows without jams or delays. So, having such a VPN will help you ensure you always deliver all your projects on time since you don’t face any inconveniences, especially if you deal with lots of audio files, videos, and images.
Paying for a VPN service that has great speeds is vital when it comes to working remotely. A high-quality VPN should ensure your work data flows without jams or delays. So, having such a VPN will help you ensure you always deliver all your projects on time since you don’t face any inconveniences, especially if you deal with lots of audio files, videos, and images.
You may also like: VPN vs RDS vs VDI: What to Choose for a Secure Remote Access?
Determining Your Standards

VPNs can be used for very different reasons. Whether you want a VPN to help you research and keep details private or torrenting after work, then you must make sure you pay for a service that provides exactly that. So, ensure you check whether it has vital features like technical security and privacy and also consider factors like customer support.
Also, some VPNs usually specialize in a particular area. Some might offer servers purposely for torrenting, while others focus more on streaming platforms. Look for a VPN that you can use for your work excellently.
Working remotely was not so common before, but you now see so many people working from home. Remote work might seem very fun, but it can be challenging if you do not have the right tools. You need a high-quality VPN to enable you to work excellently and complete all your assigned work on time. Take some time to look for a VPN that has all the vital features to avoid disappointments and ensure efficiency.
This article is written by Paul Kinyua. Paul is a professional content/copywriter that writes cybersecurity, tech, and privacy-focused articles for VPN Watch. He also loves traveling, adventures, watching movies, reading books, and exercising. You can follow him on Twitter.





