The Importance of Peer-To-Peer Proxy Networks Big Data has advanced to increase exponentially in recent years. As more photos are being taken, tagged, uploaded, and shared with the public, that is just the beginning. If you can look at a complex graph of data that is quickly updating, the eye becomes trained to instantly identify when data points are changed or when nothing changes. The brain can notice the changes in the graphs changing color, patterns, and it is almost impossible to read; you have an idea of what it would be like to look at Big Data.
This article will give you an understanding of how peer-to-peer proxy networks can keep the data around the world honest, ensuring companies are forced to be ethical. Big Data is breaking records for usage and growth, but is it ethical? The article will explain why companies shouldn’t use your private information for any purpose for fear of public backlash. Peer-to-peer networks are designed to keep the data around the world accurate and honest, ensuring companies are forced to be ethical with their choices. Therefore, peer-to-peer networks allow for privacy and anonymity while fighting against the inequalities due to Big Data.
What is this data?

Think of it as a pool of information that is constantly growing. This pool consists of all the steps you take on the internet. As you are searching the internet, you will find that there is so much information available, millions of websites, and providing data to its users. Data has grown to such a general word that many have probably never thought about its exact definition. What first pops up in our understanding regarding data is most likely a spreadsheet, a report, or a table, that contains quantities and descriptions. When everyone talks about big data, it becomes even more abstract as many bytes float through the devices and servers and require programs to decipher them.
Reasonably you have heard of the phrase “Big Data” – where companies can extract data from social media, reports, blogs, reports, and all of this data is taken to analyze the information. It has become standard practice for companies to extract data from different sources to get insight into anything from health to what online users are interested in. However, it has been apparent for some time that these large companies are not always using the data they extract ethically. Some of these companies have had their databases being hacked multiple times.
Recommended for you: How to Access Blocked Sites Without a Proxy?
What is a proxy server?
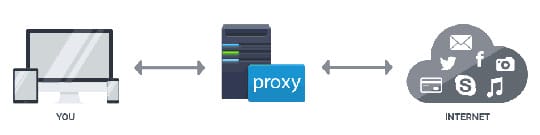
A proxy server is a machine, computer network, software, system, web service, or combination that serves as an intermediary for calls from customers querying sources from different servers. Using a proxy server provides clients with access to servers that firewalls might block because of traffic content filters. Proxy servers are a type of system used to provide a connection from one computer to another computer through an intermediate system. Proxy servers are mainly used to provide protection from network attacks and for the privacy of information. When a proxy server is being used, the user’s web browser is connecting to a proxy server for a new connection. The proxy server then connects to a destination server and sends the traffic to it. The dedicated proxy server will handle the traffic more than a normal proxy service it is necessary when handling vast amounts of data and sending it on to the destination server. A lot of people can use a proxy server as they need. The main advantage of the proxy server is that it provides privacy for the end-user and stays encrypted when using the proxy services.
What are peer-to-peer proxy networks?

In peer-to-peer networks (P2PS), a collection of processors is dec on similar permissions and data processing responsibilities. Unlike conventional client-server networks, no device in the P2P network is designed exclusively for providing or receiving data. Every connected device possesses equal claims as its counterparts and can be practiced for identical objectives. The P2P (Peer-to-Peer) Proxy network is a solution to hide your identity online by providing a unique IP address of the devices used in this network. This kind of interface indicates that after each IP is correlated to the service network, it serves as a server and dependent node without a network operating system.
P2P software such as Napster, Kazaa, etc… once continued a standard acquisition on the regular basic user’s workstation. Specific applications enabled users to share vast data of records across the internet, often movies or music. Instead of managing centralized server nodes for this view, they managed global user terminal networks as both clients and servers (i. e. P2P), effectively reducing the load on its users. Although certain applications no longer work, P2P file distribution is alive (think bit torrent and other likes). Even instantaneous messaging customers can use this feature because most of them help file sharing and chatting. However, there are many legitimate applications for P2P networks, the direction of file-sharing causes both intelligent resources problems and cybersecurity problems. People share films, games, software applications, music, or other non-free content, so questions arise about intelligent resources and copyright rules and laws.
Despite the substantial and completely statutory features that peer-to-peer can offer, many of the ISPs have tried to ban or outlaw torrents and other peer-to-peer applications. Using the end user’s device, you can balance a load of proxy network servers against users and allow the end-user to act as a dedicated server for other users on this network. Nevertheless, when working with a P2P proxy network, you need to recognize the essential hazards. With the caching system used by proxy servers, the service provider has access to protected data, browser history, and even passwords. It is constantly an excellent concept for a high-quality and trustworthy proxy service provider to guarantee privacy and security. The typical choice would be to prefer a proxy service that directly connects the internet service provider instead of peer-to-peer.
Peer-to-peer networking includes many benefits. For example, in traditionally wired networks with a client-server model, when there is a server failure, all devices in the network might shut down because the server handles all information. However, in P2P networks, when an individual device fails, the other internet devices can assist in picking up the slack. They further support ensuring traffic doesn’t become bottlenecked at one device since traffic administration is spread across several network systems.
You may like: VPN vs Proxy: What are the Differences? Which One is Better?
The big data peer-to-peer proxy network

A few major corporations own the vast majority of servers and data storage facilities, and a few major Internet Service Providers operate the majority of data storage facilities. This poses a significant security concern for consumers and companies alike. Recently, Facebook took the unprecedented step of shutting down its own servers to avoid a data breach. In light of this threat to the digital security of the world’s data, a network of peers has been created that promotes a more decentralized system of data storage. In order to maintain the strictest security possible, these peer-to-peer networks, which are made up of voluntary participants who upload and store a copy of the data, are Hercules’s task.
How the big data peer-to-peer network reduces big data abuses?

The peer-to-peer network is an excellent way to prevent abuses of big data and is becoming increasingly popular in order to exploit big data servers. The best benefit of this is that it does not need data to be stored or funneled through one central location. It further indicates that the data is more secure. Finally, the peer-to-peer network can help to balance the load on servers. The data is not collected and saved in one centralized location but instead is distributed across servers. This helps ensure that if servers are knocked out or compromised, there are others for backup. It additionally expands the load more equally across servers. This is good for any organization with many servers. The peer-to-peer network helps to prevent abuses of big data because of it.
Peer-to-peer networks are also a cheaper alternative to the current network of large data centers worldwide, making it a more affordable and practical way to store data. With this in mind, it is understandable why more companies consider using peer-to-peer networks in their data management system.
You may also like: The Advantages and Disadvantages of Proxy Server.
Big data creates an incentive for people to run proxies

Peer-to-peer proxy networks allow users to share the internet anonymously, without any centralized server. This stealthy way to harness the internet gives us the chance to see if anything in the graph has changed. You should keep in mind that these small, decentralized networks are used not only for data sharing but also other types of proxy networks. Peer-to-peer networks are best suited for these networks because they are decentralized and provide users with more privacy. Peer-to-Peer proxy networks use a decentralized architecture where all of the data is organized and organized by user-created tags and keywords. You can also search and find specific things quickly and easily. Your friends and people you follow may be able to recommend content to you through these tags and keywords.