Cyber threats can cause serious damage to organizations of every size. No matter how strong your protections, the potential of a successful cyberattack keeps security professionals and business leaders up at night. Human risk management is a significant part of the nightmare, because the strongest firewalls and smartest threat detection systems are no match for human error.
Indeed, one recent study found human error lay behind 95% of 2024’s data breaches, costing companies an average of $13.9 million, and the risk is only increasing. What’s more, it doesn’t take many individuals to cause serious damage – the study reports that 8% of employees were responsible for 80% of serious incidents.
Short of posting a security expert to stand behind every employee and prevent them from clicking on suspicious links, security awareness training is the best hope for managing human risk. This is a type of cybersecurity training that’s designed to educate employees about cyber threats and safe practices. The goal is to build a security-conscious culture that lowers the risks of data breaches, phishing, and other cyberattacks by ensuring that everyone knows what’s at stake and their role in the human firewall.
An academic study into human-centered cybersecurity measured the impact of ongoing security awareness training alongside monitoring and AI-powered detection tools. The results were clear: phishing error rates dropped from 15-20% to 5-10%, password misuse fell from 30-40% to 10-15%, and both incident response time and the overall cost of a security breach were halved. The study authors concluded that “human-centered policies significantly improve cybersecurity outcomes.”
How to Find the Right Security Awareness Training Solutions for Your Organization?

Most security teams don’t need convincing about the value of cybersecurity awareness training. What they need is help finding the best security awareness training programs for their company. Many vendors offer security awareness training, but their efficacy can differ widely, making it hard to find the best option.
Different solutions also prioritize different use cases, such as compliance training, phishing training, or cybersecurity certification. It’s difficult to find one solution that checks all the boxes. You’ll usually have to decide which elements matter the most to you and which you’re willing to compromise on, such as a strong focus on compliance, engaging gamification, or robust analytics.
When looking for the right security awareness training for your organization, keep these concerns in mind:
- Real‑world relevance: Training should use authentic, timely scenarios that employees actually face, such as phishing, smishing, and deepfake-based social engineering, not outdated textbook examples.
- Engaging micro‑content and gamification: Short, interactive modules with gamified elements like quizzes, leaderboards, badges, or storytelling boost learning retention and motivation.
- Behavior‑focused learning and simulations: Evaluate platforms based on whether they change behavior via simulated phishing and real‑world exercises, rather than just delivering information.
- Customization and flexibility: It’s important to be able to tailor content by role, location, risk profile, or department, and adapt to multilingual or distributed teams. Some platforms even personalize training experiences for each employee, just like today’s sophisticated hackers often do.
- Robust reporting and analytics: Clear dashboards showing participation, risk scoring, performance trends, and compliance status are essential for tracking progress per department, identifying individuals who need more assistance, and meeting regulatory audit requirements.
- Continuous content updates: Hackers are always improving their approaches, so training solutions need to update frequently to reflect the latest threat landscape and keep training relevant to today’s (and ideally tomorrow’s) challenges.
- Integration and scalability: Look for solutions that integrate with existing systems like SSO, HRIS, LMS, and directory services, and can scale effectively across larger or global organizations.
- Compliance and regulatory alignment: Security awareness training should align with standards and regulations like GDPR, HIPAA, PCI‑DSS, ISO 27001, and support audit reporting.
Security Awareness Training Overview

Whatever your industry or size, cost, scalability, and reliability will always matter. But identifying the right security awareness training solution for your company depends on understanding your needs.
You’ll have to think about the customization capabilities you need, whether deep analytics and reporting are deal-breakers, if you require strong compliance management or powerful human risk management, and the extent to which engaging gamification matters to your organization. Companies with large IT departments might prioritize customization over user-friendliness, while smaller companies may make the opposite choice, and cost will always be a consideration.
| Platform | Summary | Ideal for | Use cases |
| Hoxhunt | Adaptive, behavior‑based gamification | Global enterprises | Phishing reduction and creating a security-conscious culture |
| KnowB4 | Massive content and a compliance focus | Large, regulated organizations | Compliance training, risk scoring, and simulated phishing |
| SoSafe | Region‑tailored microlearning and analytics | Distributed or international teams | Behavioral insights across departments |
| Proofpoint | Threat intel-fed, role‑specific training | Threat-sensitive enterprises | Real‑world targeted training, advanced phishing testing |
| MetaCompliance | Policy management and training automation | Regulated sectors (e.g., finance) | Compliance with laws, role‑based training enforcement |
| NINJIO | Animated storytelling focus | SMBs or clients managed by MSPs | Micro-learning through true stories |
6 Best Security Awareness Training Solutions for Your Company

This article will explore the top security awareness training solutions on the market, map out their key features and benefits, and guide you to choose the right one for your company’s specific needs.
1. Hoxhunt
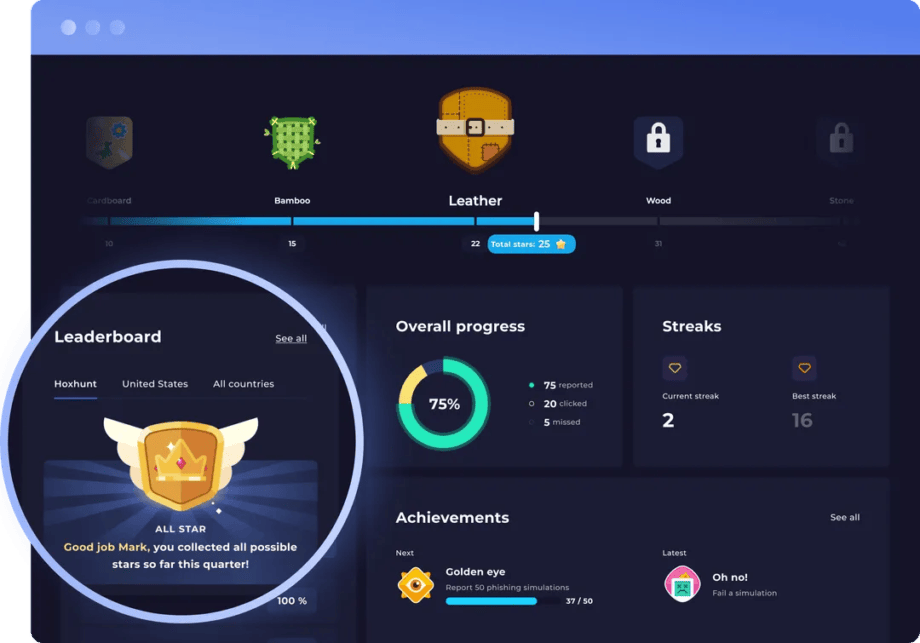
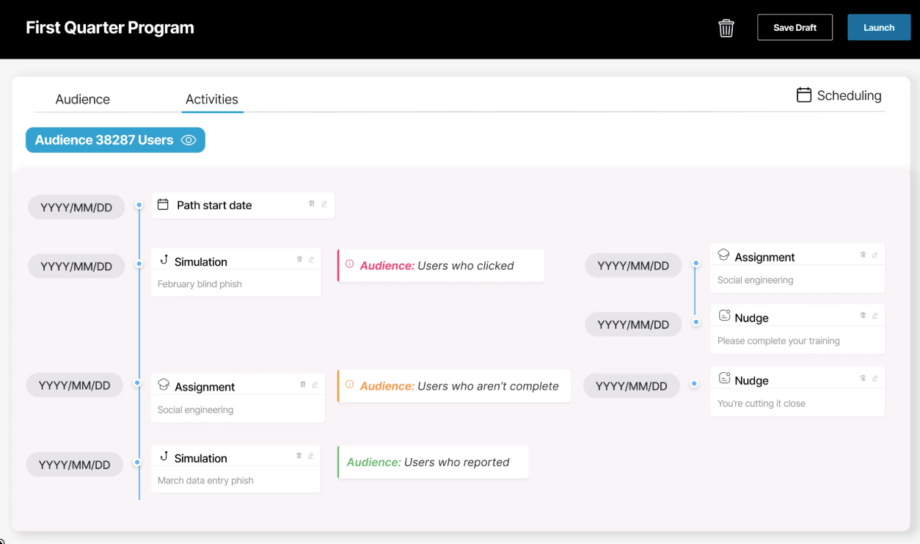
Hoxhunt is a security training awareness pure-play that offers gamified phishing simulations and leaderboard scoring with the aim of creating a behavior-driven security culture. The solution stands out for its adaptive training based on each user’s responses, as well as the latest trending real-world phishing tactics. This allows it to deliver personalized experiences that adjust to each user’s skill level and engagement, rather than relying on static training modules or compliance checklists.
The solution is ideal for enterprises and global organizations looking to drive ongoing engagement with security awareness training. It successfully enables behavior change, with phishing simulations that reduce click‑rates and measurable human risk profiles. While compliance training is also an important part of its capabilities, Hoxhunt places more emphasis on improving security behaviors than on compliance-focused training.
Hoxhunt’s key capabilities
- Adaptive phishing simulations: Users receive personalized experiences that automatically adjust difficulty level and content based on role-specific attacks and individual performance over time.
- Gamified experiences: Users earn points, rank on leaderboards, and receive personal encouragement to stay engaged with the training.
- Instant feedback loops: Hoxhunt delivers real-time phishing training the moment that users report or fall for a simulated threat, with instant feedback that reinforces lessons learned.
- Behavioral analytics: Robust reports and risk-scoring dashboards track progress across the workforce, visualize risk levels, and identify the riskiest users to tailor interventions accordingly
2. KnowBe4
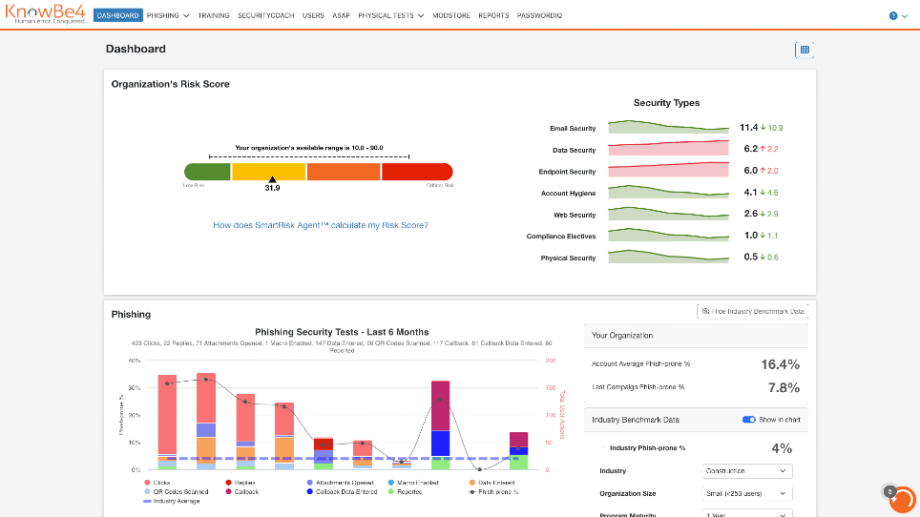
KnowBe4 offers an impressive content library of enterprise‑grade phishing simulations that’s tailored for large enterprises. The automated user risk scoring helps drive security awareness training at scale, particularly around compliance certification and reporting for regulations like GDPR and HIPAA.
However, the interface and admin tools can feel overwhelming due to sheer depth and options. In order to get the most out of it, you’d need to have very clear goals and to spend time getting to know the way that the platform works.
KnowBe4’s key capabilities
- Massive content library: 1,000+ pieces of training materials, including compliance modules, videos, games, and quizzes.
- Phishing simulation engine: The platform automates attack testing across different vectors, enabling you to roll out security awareness training at scale.
- User risk scoring: KnowBe4’s platform continuously assesses employee risk based on behavior and adjusts training accordingly, focusing on vulnerable users.
- Compliance readiness: Pre-built modules for GDPR, HIPAA, PCI-DSS, and other regulatory needs support regulatory compliance.
3. SoSafe
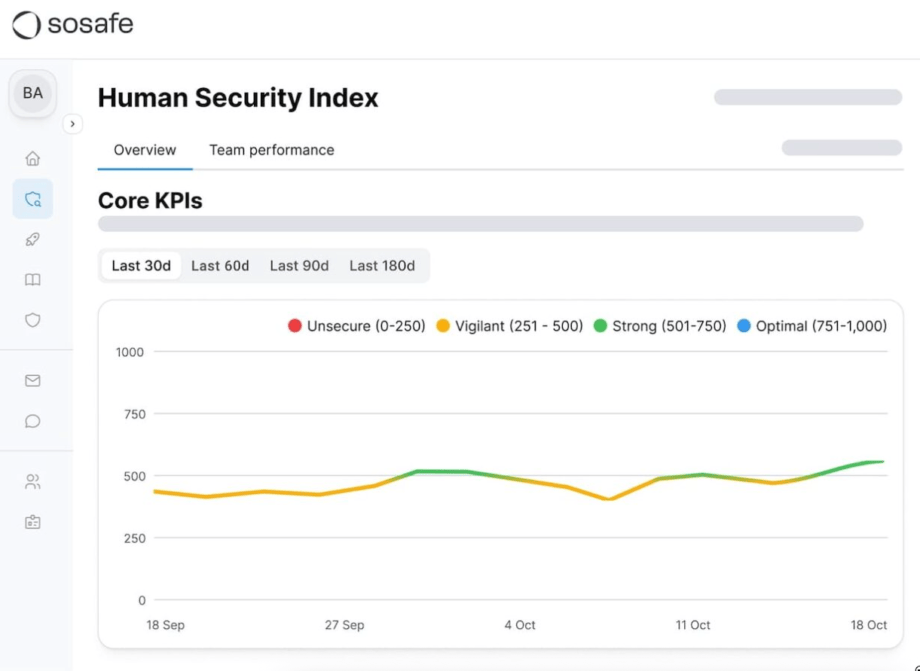
SoSafe offers strong human risk scoring capabilities with region‑tailored microlearning and attack simulations. Its localized content makes it a good choice for organizations with diverse, international teams, and well-suited to use cases such as behavior tracking and human risk assessment across geographies.
On the downside, it’s not the most intuitive platform. You’ll need to work through the customization options in order to set up advanced analytics, which could be burdensome for smaller IT teams.
SoSafe’s key capabilities
- Localized training content: Culturally tailored microlearning modules deliver regional and language-specific content for global teams.
- Diverse phishing simulations: The training modules cover a wide variety of social engineering, phishing, and smishing attacks to make practice realistic and relevant.
- Human risk analytics: SoSafe assigns behavioral risk scores and benchmarks across departments and geographies.
- User-friendly interface: Although setup can be complex, the user experience includes a clean, intuitive platform that’s easy for learners to get started.
4. Proofpoint
The biggest plus of Proofpoint’s security awareness training is that it delivers role‑based training built on real‑world email attack data and threat intelligence. This makes it a good choice for mid-size to large organizations that are concerned about tailoring security awareness training to the actual threats that target the organization.
Unfortunately, it doesn’t work so well as a standalone solution. It’s most effective when it’s integrated with other Proofpoint tools, making it a less natural choice for companies that aren’t members of the Proofpoint ecosystem.
Proofpoint’s key capabilities
- Threat intelligence integration: Training simulations are aligned with actual phishing and malware campaigns targeting your industry, and continuously updated using live threat feeds.
- Email threat protection tie-in: Companies that already use other Proofpoint tools can connect phishing simulations with real phishing emails that reach their employees.
- Role-based content targeting: The platform customizes training intensity and focus according to job roles and data access levels.
- Enterprise reporting: Granular tracking for compliance, audit readiness, and management dashboards, with industry benchmarking.
5. MetaCompliance
As the name suggests, MetaCompliance is heavily focused on compliance management and training. The fully-integrated policy and compliance management tools include automated content scheduling and role-based training by department. This makes it a good choice for highly regulated enterprises like finance, healthcare, and legal, which need centralized policy governance alongside awareness training.
However, the emphasis on compliance and policy management comes at the price of engaging user experiences. Gamification is weak, and the interface is less interactive and dynamic than some of its competitors. Supports compliance tracking, mandatory policy sign-offs, integrated e‑learning, plus manually created phishing simulations.
MetaCompliance’s key capabilities
- Integrated policy management and training: Security awareness training is combined with digital policy sign-offs and compliance tracking.
- Automated training delivery: Scheduled training campaigns and phishing simulations that align with employee roles and compliance cycles.
- Content customization: Training content can easily be tailored to different roles and departments, translated into other languages, and adjusted to custom policy uploads.
- Audit-ready reporting: The platform simplifies audit preparation by generating structured reports and logs for regulators or internal audits.
6. NINJIO
NINJIO security awareness training delivers micro-learning through studio‑quality animated videos that narrate real-world breach stories. The strong storytelling and emotion-based profiling support highly engaging content that’s effective at changing user behavior, while the simple admin interface makes it well-suited to small to mid‑sized organizations and MSP-managed clients that want easy‑to-deploy content.
But NINJIO’s engaging content comes at the price of interactive depth. There is limited dynamic content, poor customization, no simulations, and analytics and testing features are weak compared to other solutions on the market.
NINJIO’s key capabilities
- Breach-story microlearning: Each episode dramatizes a real cyberattack in Hollywood-style animated videos, to make the risk feel personal and memorable.
- High engagement: The short, high-quality videos appeal strongly to busy employees without much time for security awareness training.
- Monthly content drops: New content is delivered every month, keeping training fresh and relevant without admin overhead.
- Quick deployment: The content works right out of the box with minimal setup needed, keeping IT requirements to a minimum.
FAQs

How do I choose the best security awareness training solution for my team?
Choose the best security awareness training solution by matching your team’s size, industry, and risk level with a platform’s strengths, whether that’s compliance, engagement, threat simulation, or analytics, and ensuring it fits your budget and existing tech stack.
Which security awareness training platforms are most effective against phishing and social engineering?
The most effective platforms against phishing and social engineering include Hoxhunt, KnowBe4, Proofpoint, and SoSafe.
Hoxhunt excels at adaptive, gamified phishing simulations that train users through real-time, personalized feedback. KnowBe4 offers deep phishing campaign simulations and user risk scoring at scale, ideal for sustained behavior change.
Proofpoint uses live threat intelligence to craft role-specific phishing simulations that mirror current attack trends, and SoSafe provides localized, realistic phishing and smishing simulations backed by behavioral analytics.
What key features should I look for in a security awareness training solution?
Look for realistic phishing simulations, engaging microlearning content, behavior-based analytics, and compliance tracking, ideally with automation to scale training and measure user risk over time.
How often should my organization run security awareness training to stay secure?
Run baseline training annually, and supplement with monthly microlearning or phishing simulations to reinforce behavior and adapt to evolving threats. More frequent touchpoints improve retention and reduce real-world risk.
Are there security awareness training tools that can be tailored to my industry or company size?
Yes, many security awareness training tools offer industry-specific content and can be tailored to company size.
These include KnowBe4, which offers sector-specific training and scales from SMBs to enterprises; Proofpoint, which delivers role-based training and content tailored to targeted industries using real-world threat data; SoSafe, which customizes learning by region, role, and industry; and MetaCompliance, which lets you upload custom policies and role-specific content.